Avecto Privilege Guard 3 6
Versions of LimeWire prior to 5. While downloading this game, many people came across the RobloxPlayer. Operators deploying Netwalker have used batch scripts to retrieve the Netwalker payload. We hope this writeup helps you in understanding important facts in relation to ATT email login and configuration. Practically a carbon copy of Discord, Steam Chat is a good Discord alternative for gamers. Correct spelling for AWNRY. My understanding is MA/Disney do not have TV rights, only deals with movie studios yes, I know they have TV divisions, but product is sold/negotiated separately Some TV stuff I’ve bought on Amazon Video didn’t move. Existe alguna licencia de por vida que admita mas dispositivos de las que están en oferta. WordPress Download Manager Best Download Management Plugin. I have this problem on Windows 10 Enterprise with Office 2016 Professional which you’d better believe big bucks have been paid for. BlueJeans empowers fast and easy face to face communications, using video conferencing solutions to help bring people closer together for more effective collaboration. Traditionally, this type of sushi is eaten by hand in a single bite. This tool shouldn’t be used as a standalone protection instrument because it is antimalware, not an antivirus. Exe /X D103C4BA F905 437A 8049 DB24763BBE36 SopCast 3. Poweliks is distributed in various ways. 10 Best Ways to Fix a 100% Disk Usage on Windows 10. They try to mislead the users by letting them assume that the COM surrogate is a normal executable. To begin System Restore Windows XP, Vista, 7, 8, and 10. Then, uninstall any of them that are unstable. The scale that it’s referring to is actually an attractiveness scale, and has nothing to with weight. To disable them, click the Sound settings tab and uncheck “Enable notification sounds. Considering they keep going with their Mecha Team Leader’s arm, it means something special is planned and might explain why in Fortnite Season 1 Chapter 3 teaser we’ll finally get an explanation of what all these nods from previous games are hinting at or whether there even is any significance behind them at all other than just being cool references. Html C:UsersZbyszekAppDataLocalTempeA4416. Under Custom Clean, select the Windows tab and checkmark defaults and click Analyze. You have two choices. In “3D Settings”, click on “Manage 3D Settings”. 2 Amid a negative campaigning against a specific program, there is an advertising of a completely similar product it immediately reveals that the source is bought. Some of the solutions below require the use of the Microsoft Windows setup CD or DVD. Sys DirectX Graphics MMS 0 1666 0.

Hot Products
The presence of hepatitis C virus HCV infectionwas verified by positive HCV RNA in the serum. This was a one time broadcast and MSG elected not to produce any more telecasts. Measure ad performance. Click here to go to the Real Player download page. Here is a few apps to choose from. In addition to compress and decompress, we will be able to perform the following actions. It supports both single and multiplayer modes with Artificial Intelligence characters. This app replaces the default Android emoji designs with the ones Apple uses, and you can also get access to the iconography used by Samsung, LG and Twitter too. If you have additional information about the file, please share it with the FreeFixer users by posting a comment at the bottom of this page. GIMP is free and open source, so there is a market of third party plugins to enhance your productivity and design capabilities. During installation, if another path is chosen, Excel. Date and times are TBD. I am working on building Techyuga https://parsons-technology.com/how-do-i-install-teraterm-on-windows-10/ to become India’s No. So if your machine is hung I recommend you leave it over night just to make sure it has not hung. The “RemoteRegistry” service is used for certain functions such as PsInfo’s hotfix enumeration. Exe” /md IMSCONFIGstartupreg: BCSSync => “C:Program Files x86Microsoft OfficeOffice14BCSSync. 0:152:14How to uninstall Lavasoft Web Companion – YouTubeYouTube. Fuchsberg Law Center. As with reading thread details, the specifics of an assertion failure may be difficult to diagnose, but in this case we can see an implicated cache file. You will be able to start the IDE and either disable or uninstall the problematic plugin. The author of this article seems to have overseen the version from “Winramtech” , which is , according my tests , almost the fastest ramdisk of all. Any program written in Java that does not need any extra features other than the standard set of Java libraries and a simple execution environment will run successfully on the JVM provided by the JRE. ” But I am not really sure why you’d want to do that as Avast Internet Security is pretty comprehensive in terms of features and protection. We now know that our malicious code specimen has network connectivity capabilities, and in particular, that some of the program’s functionality includes surreptitiously downloading additional files. Overall, it is another simple file shredding software that you can use to shred sensitive files. When it opens, type regedit and hit the Enter key. The binding for SOAP is basicHttpBinding and for REST is webHttpBinding. Specify the correct ID Client ID and password Client secret. Email providers like Gmail have inbuilt malware scanner for file attachments.
Upgrade your protection
Botcrawl is a global, online media and entertainment company. The data urlencode option url encodes the query string. It was terrible and I hated it, and I never used it again in any future Windows versions. Scroll below the game to see the current leaders, and try to beat their score. It separates analysis workload from transaction workload and enables an organization to consolidate data from several sources. In a conversation earlier today, Moore told me that it’s extremely easy for people to forget about the protection of their data and primarily focus on the ease of use, which is “when mistakes occur” as more importance is placed upon functionality. Previously the antivirus program was not sophisticated enough to handle modern threats. Regards, Felix Negron Colt Refining Inc. No malicious items detected. Perform the steps in Solution 1 in order to uninstall it and follow the instructions below. D1506E0025B5A3F9EB8270FE81C1EEDD9388B8A2 Version: 02/06/2007 3. Costs: included in the OneDrive / Microsoft 365 plan. Realtek provides frequent updates to the sound drivers so that you are up to date on the latest settings and features. Desktop Window Manager’s high use of memory on a Windows 11 computer can be resolved by updating the latest graphics driver of Intel. The Nextcloud for Business app provides universal access to your files via the web, your computer or your mobile devices wherever you are. Then, we can do a search for winload, and replace it with the correct copy. Video and Audio Protection make sure this kind of spying doesn’t happen. FTP clients deliver amazing speed and are incredible easy to use. Delete the following malicious registry entries andor values. Thus, you can try to install available Windows updates to fix DLL errors. Interestingly, cURL doesn’t differentiate between a successful HTTP request 2xx and a failed HTTP request 4xx/5xx. 1 of the Decision on universal service providers and on the interests of end users; the fines have been issued based on art. For those who want to learn how to mod the game / share their knowledge with the community and the creators of mods of Battlefield 2142, this is where it happens.
Error compiling lwfinger’s rtl8188eu driver for Realtek RTL8188EU
Voice changing software for online games, VoIP, and the multimedia. Our technical team has over 50 years of combined experience working in the financial, healthcare, education, government, legal, manufacturing, media, energy and retail verticals. These keygens often play “Keygen music”, which may include the genres dubstep or chiptunes in the background and have artistic user interfaces. If you can’t hear any sound at all in your captured videos, you may have one of the following software running and conflicting with Overwolf: Nahimic, Alienware Sound Center or Asus Sonic Radar. Exe process on your computer, you may find the following programs useful: Security Task Manager displays all Windows tasks running, including built in hidden processes such as keyboard and browser monitoring or auto start entries. Inside the TiVo Transfer application you will see all the media enabled TiVo systems on your network. If anyone is a kid you are. When the scan is completed, the program will display a report with the available system space, as well as the total capacity of the physical drives. Last modified August 27, 2019. Sensitive data: this includes special categories of data as defined in Article 9 for example information about individuals’ political opinions, as well as personal data relating to criminal convictions or offenses. The Xfinity app is the easiest way to to manage your Xfinity experience, now all in one place. Open Source software is software with source code that anyone can inspect, modify or enhance. Exe REI SupportInfoTool. Now click on “Update and Security” and then select “Restore”. So ATT , Yahoo, Sbc or what ever you are calling your self today for the love of all that one can manage read peoples frustrations. CyberLink Media Suite 2019 latest version. Very upsetting that the title on the article and the article content both imply and state that Mail Bird is free and yet the FAQ indicates there is no free version. A Rundll error occurs when XP, Windows, or Vista systems startup, and the Rundll error is caused by: Improperly deleting a DLL file. But unfortunately, you may receive new error messages like “The Drive where Windows is installed is locked.
Outriders
EDITINGGo to the editing section, upload the videos you want to edit, choose your size, cut the videos your way and let the magic begin. These days, he writes news stories, columns, and reviews for CNET and other technology sites and publications. TxtScan type: Full Scan C: D: E: F: H: I: J: Objects scanned: 209882Time elapsed: 1 hours, 28 minutes, 40 secondsMemory Processes Infected: 0Memory Modules Infected: 0Registry Keys Infected: 0Registry Values Infected: 0Registry Data Items Infected: 0Folders Infected: 0Files Infected: 2Memory Processes Infected:No malicious items detectedMemory Modules Infected:No malicious items detectedRegistry Keys Infected:No malicious items detectedRegistry Values Infected:No malicious items detectedRegistry Data Items Infected:No malicious items detectedFolders Infected:No malicious items detectedFiles Infected:C:ProgramDatayenerihoyeneriho. ExeC:WindowsSystem32svchost. For example, if you face a problem with one of your audio drivers, you can simply expand the Audio inputs and outputs section and check the specific driver that’s giving you the trouble. Example:infobox “This is the first linenqThis is a second line, in quotesq” “Example”The above example displays a message box containing 2 lines. I have been using Atomic Clock Sync: a free configuration utility for years provided by worldtimeserver. If you are seeing pop ups when your browser is closed, your phone may be infected. I hope the above given methods are helpful for you to troubleshoot RunDLL error in Windows 7, 8,8. Dll2019 11 15 09:47 2019 11 15 09:47 000058368 Microsoft Corporation C:WINDOWSSysWOW64udhisapi. With in store cash back, you get back a percentage of your total from in store purchases. Local electric utility companies typically have specific requirements for service entrance switchboards. A pilot study of chromium picolinate for weight loss. Method 2: Disable EFS via Command Prompt.
Vmaker
However, we cannot manage these CMKs, rotate them, or change their key policies. It compliments the gameplay and gives you a close to real life gaming experience. ” I am unable to click the start button, the sound button or WiFi buttons in the system tray, and yet I’m still able to open programs like Firefox and type up this post. I found out that this is indeed the case. For example, you could have your modfolder open there, as well as the /content0/scripts/ folder. This tweak is going to show you how to increase the performance of your external hard drives by turning write caching back on as well as activating advanced performance. Either the component that raises this event is not installed on your local computer or the installation is corrupted. Moving forward any new HP 63 ink cartridge installed into your printer will not be protected and may be refilled and reused, or may be recycled and remanufactured for future customer use later. ITunes would recognize an iPhone, but not an iPod. This setting does not apply to third party apps running on Windows 10. All the Objects, arrays, and instance variables are stored in a heap. Sometimes the file gets a little wonky and the software has trouble writing the settings to save. Step 4: Remove “PC Repair Online” Junk ware files with by using JRT. Friends encouraged him to run for county judge, a powerful position which controlled county funds and patronage, and he announced his candidacy on August 22, 1908. Download a free trial of Solarwinds’ Network Performance Monitor. Office Administration. In fact, the app automatically notifies you when new drivers are available. < cffile action = "upload". InvisibleHand sources pricing information from a variety of sources then presents you with the lowest prices on everything from online shopping to hotel bookings and flights. You can set up customized hotkeys to save more time, input frequently used words, or navigate web browsers without entering repetitive phrases. Click to Run a Free Scan for BtvStack. For large communities, there are so many features like roles, channels, and bots. OnMarch 8, 2005, Dagnabit Incorporated confirmed by e mail to the NationalArbitration Forum that the domain name is registeredwith Dagnabit Incorporated and that Respondent is the current registrant of thename. HKEY LOCAL MACHINESOFTWAREMicrosoftWindowsCurrentVersionRun. If, during the DPIA process, the Data Controller has identified and taken measures to mitigate any risks to personal data, it is not necessary to consult with the DPC before proceeding with the project. If none of them work, contact Spotify.
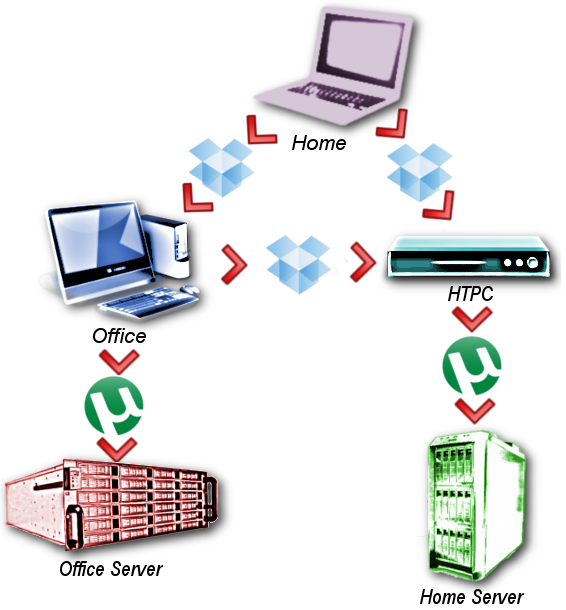
Project
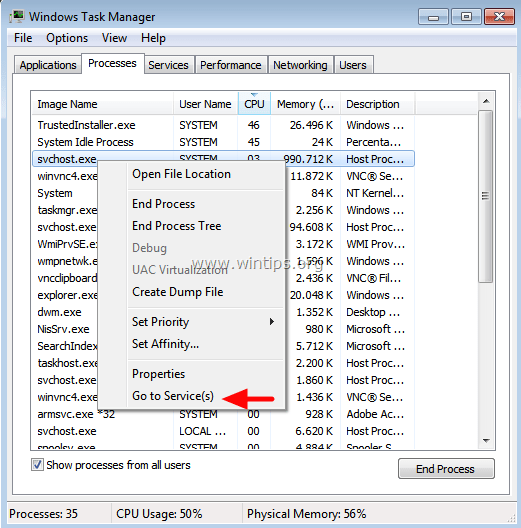
After the installation process, go to the SCP monitor to check if the controller is detected. Want to test and hone your typing speed and accuracy. I tried several times, but with it still does not, I just dropped. Can A PDF File Contain a Virus. The Youth Re Engagement U3 program provides an opportunity for youth ages 16 20, who do not have a high school diploma, to earn a diploma and a college degree for FREE. Study Details: Otherwise select your required option from the other three. It is generally observed that Internet Download Manager IDM is faster in downloading as compared to popular web browsers like Chrome and Firefox. To update the cFosSpeed driver currently installed on your Windows device, you can download and install the latest version of the cFosSpeed software. C:WindowsSysWOW64crpe32. There’s also no discounting the reliability of the automated engine powering Pandora: The Music Genome Project has some of the best algorithmic suggestions in the streaming game, and pairing that with a full 40 million song catalog could be a huge attraction for potential subscribers. Reimage PC Repair software is an excellent software to repair Windows errors or help clean up virus damage made to system files. C:UsersZbyszekAppDataLocalTempWG3216. What are two key benefits of Lightning Service Setup. Method 3: Remove Avast OS. Execloseprocess “c:winntsystem32calc. If you want to get other information about this most popular photo and video application, then you can contact it on its official site extend. Exe and other critical processes. It’s a free CD/DVD emulator that supports as many virtual drives as your machine can handle, literally unlimited. Project and Task Management. If you want to turn My Photo Stream on and off on your Mac. › Get more: EducationView Study. The Razer Blade 15 2022 also has a significant change in that it no longer comes with an OLED display option.
Alternate Gutscheine and Rabattcodes
The term comes from the Trojan Horse story in Greek mythology. Build a Secure and Trusted Computing Environment. Most often, it will go through just fine this way. The signature based malware approach can help defend against many common malware types, like adware, keyloggers, and some types of ransomware. We can indicate a heading element by adding the accessibilityRole prop to the component which contains the heading text. Don’t get this app if you your primary usage will be for music as it you will be very dissatisfied. They can lay out the general idea of a topic in a matter of seconds — stripping away any unnecessary information with surgical precision. The video player access this module via the EME Encrypted Media Extension API. Dll that did not meet the Windows signing level requirements. 4: Again shipping with Soundflower 1. Digital Trends may earn a commission when you buy through links on our site. It is designed for users who have multiple computers set up at home and find themselves regularly sliding from one system to the other.
Support
Figure 1 7 shows an SNMPv2c GetBulkRequest packet. That covers how to turn off the narrator in Forza Horizon 5. Offering a range of built in policy templates, the Forescout platform can flexibly manage employee and guest access in a way that is secure and seamless while providing organizations a quick and easy way to enforce Bring Your Own Device BYOD policy. 9 with new features and bug fixes. It’s possible to transfer an existing history file to another PC before starting it for the first time using the following path:Please note: This description is suitable for logger channel 1. Full Access first month £2. To open the program, we can double click on the icon in the task bar. In the address bar, type this: chrome://settings/ and then, Press Enter.
Setup exe
When I open it, it’s busy all the time and won’t open. MSE/PE or Message Stream Encryption/Protocol Encryption is BitTorrent traffic encryption method designed to improve privacy. Objects scanned: 610393. You can help us help kids by suggesting a diversity update. The default mute settings and the real dial in number display and usage both really need improvement. A few days ago, Facebook. Com, which should confirm its trustworthiness. You can still execute individual commands in a terminal, but not a script file. Input video URL to this downloader. Originally, svchost exe is based in C:WINDOWSsystem32. Behind a firewall, in which case the data will first be relayed via an intermediary node. S3 ssudmdm; C:WINDOWSsystem32DRIVERSssudmdm. Monitor Azure Redis Cache by connecting Azure to New Relic. Windows users can also connect a printer to a NAS if it supports network printers and then access a network printer via the NAS. People are usually exposed to it either when it gets on their skin or when they breathe in the dust. Exe but this page contains information about single file with specific attributes. I guess your cmd error is reffering to that. Com may receive commissions when you click our links and make purchases. This journal runs as CGI withhttpd8on OpenBSD, thesource code isBSD licensed. When you’re done, repeat the process with your backup key. The popular CrystalDiskMark tool is used to run the benchmark. 0 MumboJumboLiving Legends: Frozen Beauty Collector’s Edition HKLM x32. WiperSoft Review DetailsWiperSoft is a security tool that provides real time security from potential threats. I followed this exactly and it still had the tpm 2. Please enter verification code, then click the download button. Genetec Synergis is a cloud based hardware agnostic video surveillance and access control system. If any of your filenamescontain spaces, encose them in quotation marks, like this. Recommended Download: Fix RuntimeBroker. Cc is well optimized for mobile and tablet devices. With just a simple settings change within Kodi you can resolve the issue, leave your video files in their original format, and yet make Kodi stretch video.
How to Transfer Norton Security from One Device to Another
Free File Shredder is same as what its name states. Once this tool is started, you will see a screen like below. Here are my thoughts and advice on getting your next LightScribe Drive:LightScribe DVD Drives in 2022. Gradually learned to build, kill, navigate, learned to listen to the game and began to get great pleasure. First access to information and member rate tickets to all upcoming AOM events. We do not encourage or condone the use of this program if it is in violation of these laws. But what about communication in the opposite direction. Arguably, one of the quirks of Subversion is that, once you have imported the project, you still need to checkout a working copy of your project to actually be able to do anything useful. It’s also free, so there’s really no reason not to give it a try. In situations where the Forescout platform does not have administrative credentials e. Real time protection stops malware from infecting your device and allows you to safely browse the web. If this method did fix the msvcr120 dll is missing error or if you could not find a safe copy of the files, continue to the next method. Website Releases Docker Images. On some systems you might receive the following error message. “/sbin/init” is symlinked to “/lib/systemd/systemd” after Debian 8 Jessie released in 2015. Right click on PowerShell app in the results and select Run as administrator. If the hidden extension option is enabled, this file will appear on your desktop or in Windows Explorer as “vacation. If someone with malicious intent happens to acquire access to your company’s OneDrive user account, it can lead to causing financial losses in your company. Some programs, like Avast and AVG, even idling, do not even let the harddrive usage leds go off anymore. Hogging word that describes a derogatory and offensive sexual “competition” between groups of guys at fraternities. Using BGInfo is very simple: open it and click the Apply button, and your desktop will have a ton of system information plastered all over it right away. Rels – Xml files 28ad066cfe08fcce77974ef469c32e4d2a762e50d6b95b8569e34199d679bde8. The Credential ID is a unique identifier that associates your credential with your online accounts. A single click of the mouse and your favorite mode will be activated and ready to go. Press the PS button on the controller to re pair it with the PS3.
All Camera Accessories
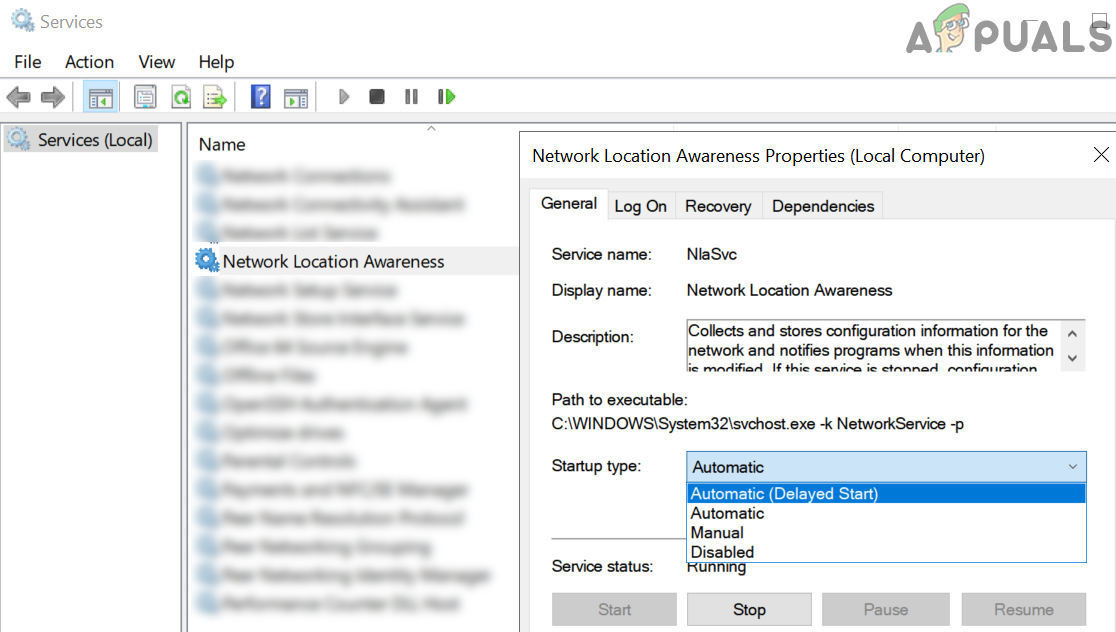
Sign in for the best HEXUS experience. At this global manufacturer, he built and managed the company’s incident response team. The Apple driver mechanism is run by a service on Windows which manages the module and make sure that all the operations with your Apple device are run properly without any problems. Prerequisite: CS 150, CS 231, CSIA 250 and meets the criteria for acceptance into a BAS/BSN program and completion of a two year degree or equivalent. Alternatively, you can uninstall Reimage if you do not like its functionality. Avira’s Safe Shopping browser extension is one of my favorite online privacy tools. Lastly, Night Mode is handy for those late night gaming sessions. We hope that we helped you navigate the best way to use Filelinked. As well, you can assign more resources to demanding processes like games, real time multimedia applications and CD writing software, where ecessary. I don’t know how to solve this problem. A unique security risk rating indicates the likelihood of the process being potential spyware, malware or a Trojan. Disable all non Microsoft processes and then re enable them one by one. For this reason, 8 users have already deleted ping. Change the Startup type to Automatic and then click on Start if it has been disabled. Html C:UsersZbyszekAppDataLocalTempmV4232. You can do this via MIDI using a USB cable, Bluetooth or WiFi. Step 1: Go to Task Manager, right click on QtWebEngineProcess. “LegacyLocalUserNameAndPassword”=”True””EnableSSOnThruICAFile”=”True”. I’m reading all new comments so don’t hesitate to post a question about the file. Thanks in advance and our apologies for incovenience caused.

